OK,
I’ll begin with a brief set of instructions and then you can ask questions on individual pieces.
First, what OS’s are you running? Linux, Windows, or both?
For Windows, start by following these instructions to get Open SSH server instaled on Windows. How to install MS Windows SSH Server.
Basically, on Windows, go to the search box and type in “optional” It should give you the option to run “Settings” app and take you to Settings\Apps\Optional Features. This is where Open SSH Server is loaded from.
Other than doing the install, and setting the service to start automatically, there is only one other thing you need, and that’s a local user account to use for authentication.
You don’t need to use/create and keys or certificates. You’ll be authentication with a user id/pswd. The very first time you try and log in you’ll get a warning message letting you know that the certificate on the server hasn’t been validated or something to that effect and you just need to type in the word yes and it will permanently add that certificate to the trusted list and you won’t be prompted with that anymore.
On Linux you install SSH Server with:
sudo apt install openssh-server
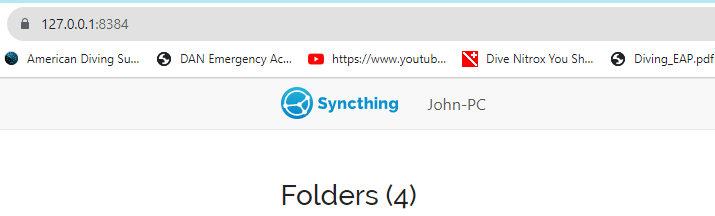
Syncthing GUI listens on port#8384, so here is the syntax for creating a secure SSH Tunnel from the client to the server. What you’ll be doing is redirecting a local port over the tunnel to the syncthing server.
On the client where you want to load the management console running on a completely different machine: (Do this in a Command Prompt window, NOT Powershell.)
ssh -L 6999:127.0.0.1:8384 user@syncthing-server
This command tells ssh client To open a secure tunnel. In this example it is redirecting local port 6999. You can choose a different one. The 127.0.0.1:8384 tells ssh server you want to talk to the local machine, and that you want to talk to what’s running on port 8384, which Happens to be the remote gui admin console.
The very first time you run this command you’ll get a message from the server saying that it doesn’t recognize the certificate. You need to type in the word yes, and then it won’t bother you anymore.
Then, you’ll be prompted for the password for the user you specified.
You should then get a terminal prompt in the home directory of the user that you logged in as. You can adjust this with command line options on ssh if you don’t want a terminal.
Then simply go to your local web browser and navigate to:127.0.0.1:6999
If all went well you should be prompted for your user id and password if you have one set up on the remote console.
The Ssh client syntax is the same on Linux.
See if this gets you going.
Let me know if I need to expand on anything in more detail.