MrChuw
July 1, 2023, 5:45pm
1
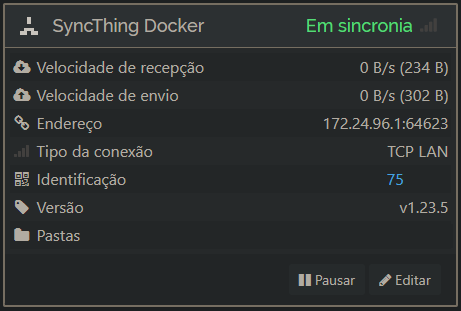
On my computer, I run two instances of Syncthing, one through the exe on port 8385 and another in Docker on port 8384. It works perfectly fine, until today when, for some reason, I decided to remove the container to make some configuration changes. After removing it and modifying the settings in the docker-compose.yml file, I tried to bring it up again. It connected to the relay without any errors, but when I tried to access the web UI, it didn’t work.
version: "3"
services:
syncthing:
image: syncthing/syncthing:latest
container_name: Syncthing-Docker
hostname: SyncThing Docker
environment:
- PUID=1000
- PGID=1000
volumes:
- E:\Syncthing Docker:/var/syncthing
network_mode: host
restart: unless-stopped
gadget
July 2, 2023, 12:27am
2
MrChuw:
On my computer, I run two instances of Syncthing, one through the exe on port 8385 and another in Docker on port 8384. It works perfectly fine, until today when, for some reason, I decided to remove the container to make some configuration changes. After removing it and modifying the settings in the docker-compose.yml file, I tried to bring it up again. It connected to the relay without any errors, but when I tried to access the web UI, it didn’t work.
Which hypervisor is being used to host the Docker container?
MrChuw
July 2, 2023, 5:38am
3
Server: Docker Desktop 4.20.1 (110738)
Engine:
Version: 24.0.2
API version: 1.43 (minimum version 1.12)
Go version: go1.20.4
Git commit: 659604f
Built: Thu May 25 21:52:17 2023
OS/Arch: linux/amd64
Experimental: false
containerd:
Version: 1.6.21
GitCommit: 3dce8eb055cbb6872793272b4f20ed16117344f8
runc:
Version: 1.1.7
GitCommit: v1.1.7-0-g860f061
docker-init:
Version: 0.19.0
GitCommit: de40ad0
And wls2.
gadget
July 3, 2023, 12:28am
4
MrChuw:
And wls2.
WSL 2 (Windows Subsystem for Linux 2) uses an Ubuntu Linux installation for hosting Docker engine.
Your revised YAML file looks normal and you said that you saw a connection to a Syncthing relay, so that makes me think it’s a firewall issue either inside the Ubuntu Linux virtual machine or on the Windows side. But it could also be that Syncthing inside the Docker container is shutting down after trying a relay.
Verify that the Syncthing Docker container is still running when you try to access it.
Verify that the Syncthing Docker container is actually listening to port 8384.
If both steps 1 and 2 are true, then you must rule out firewall and malware scanner issues.
Personally, I’d roll back all changes since it was last working to rule out the container and Docker.
Although you didn’t mention it, I’m assuming that the Windows instance of Syncthing is still accessible on port 8385 and that access is only from the Windows host and not from another device on the LAN.
MrChuw
July 3, 2023, 5:27am
5
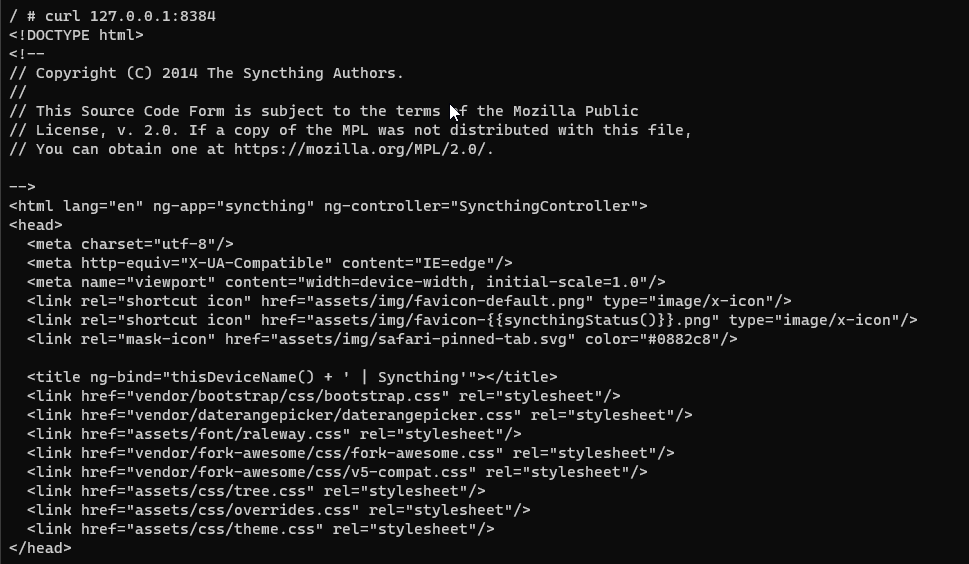
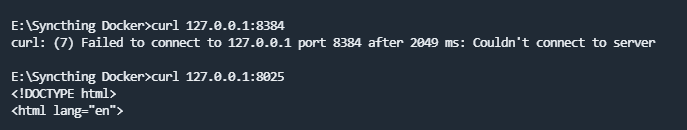
I can modify the settings to add the Windows instance and my cellphone, and I can even use curl on other containers and even on my Raspberry Pi.
I tested curl on port 8384, and it worked. I also tried changing the port in the .xml file and tried again, and it worked too.
I could use it by just editing the .xml file, but you know, adding a folder would be such a hassle instead of just clicking “accept.”
Since cURL is able to access Syncthing’s web GUI, what doesn’t work? Did you mean you get an error in a web browser?
MrChuw
July 3, 2023, 3:37pm
7
Sorry, I expressed myself poorly. I can use cURL from within the container to the outside, but I can’t do it from outside to inside.
The first one is the port of Syncthing, and the second one is another container.
The first one is the port of Syncthing, and the second one is another container.
Ah, no problem. In the Syncthing container, what is the output from the command ufw status?
And from the Windows host, does netstat -an show a process listening on port 8384?
MrChuw
July 3, 2023, 4:57pm
9
gadget:
netstat -an
Port 8384 does not appear in netstat.
gadget:
ufw status
iptables -L Output
Chain INPUT (policy DROP)
target prot opt source destination
ufw-before-logging-input all -- anywhere anywhere
ufw-before-input all -- anywhere anywhere
ufw-after-input all -- anywhere anywhere
ufw-after-logging-input all -- anywhere anywhere
ufw-reject-input all -- anywhere anywhere
ufw-track-input all -- anywhere anywhere
Chain FORWARD (policy DROP)
target prot opt source destination
DOCKER-USER all -- anywhere anywhere
DOCKER-ISOLATION-STAGE-1 all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
DOCKER all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
DOCKER all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
DOCKER all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
DOCKER all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
DOCKER all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
DOCKER all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
DOCKER all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
DOCKER all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ufw-before-logging-forward all -- anywhere anywhere
ufw-before-forward all -- anywhere anywhere
ufw-after-forward all -- anywhere anywhere
ufw-after-logging-forward all -- anywhere anywhere
ufw-reject-forward all -- anywhere anywhere
ufw-track-forward all -- anywhere anywhere
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ufw-before-logging-output all -- anywhere anywhere
ufw-before-output all -- anywhere anywhere
ufw-after-output all -- anywhere anywhere
ufw-after-logging-output all -- anywhere anywhere
ufw-reject-output all -- anywhere anywhere
ufw-track-output all -- anywhere anywhere
Chain DOCKER (8 references)
target prot opt source destination
ACCEPT tcp -- anywhere 172.18.0.2 tcp dpt:9443
ACCEPT tcp -- anywhere 172.18.0.2 tcp dpt:9000
ACCEPT tcp -- anywhere 192.168.80.2 tcp dpt:mysql
ACCEPT tcp -- anywhere 192.168.16.2 tcp dpt:8025
Chain DOCKER-ISOLATION-STAGE-1 (1 references)
target prot opt source destination
DOCKER-ISOLATION-STAGE-2 all -- anywhere anywhere
DOCKER-ISOLATION-STAGE-2 all -- anywhere anywhere
DOCKER-ISOLATION-STAGE-2 all -- anywhere anywhere
DOCKER-ISOLATION-STAGE-2 all -- anywhere anywhere
DOCKER-ISOLATION-STAGE-2 all -- anywhere anywhere
DOCKER-ISOLATION-STAGE-2 all -- anywhere anywhere
DOCKER-ISOLATION-STAGE-2 all -- anywhere anywhere
DOCKER-ISOLATION-STAGE-2 all -- anywhere anywhere
RETURN all -- anywhere anywhere
Chain DOCKER-ISOLATION-STAGE-2 (8 references)
target prot opt source destination
DROP all -- anywhere anywhere
DROP all -- anywhere anywhere
DROP all -- anywhere anywhere
DROP all -- anywhere anywhere
DROP all -- anywhere anywhere
DROP all -- anywhere anywhere
DROP all -- anywhere anywhere
DROP all -- anywhere anywhere
RETURN all -- anywhere anywhere
Chain DOCKER-USER (1 references)
target prot opt source destination
RETURN all -- anywhere anywhere
Chain ufw-after-forward (1 references)
target prot opt source destination
Chain ufw-after-input (1 references)
target prot opt source destination
ufw-skip-to-policy-input udp -- anywhere anywhere udp dpt:netbios-ns
ufw-skip-to-policy-input udp -- anywhere anywhere udp dpt:netbios-dgm
ufw-skip-to-policy-input tcp -- anywhere anywhere tcp dpt:netbios-ssn
ufw-skip-to-policy-input tcp -- anywhere anywhere tcp dpt:microsoft-ds
ufw-skip-to-policy-input udp -- anywhere anywhere udp dpt:bootps
ufw-skip-to-policy-input udp -- anywhere anywhere udp dpt:bootpc
ufw-skip-to-policy-input all -- anywhere anywhere ADDRTYPE match dst-type BROADCAST
Chain ufw-after-logging-forward (1 references)
target prot opt source destination
Chain ufw-after-logging-input (1 references)
target prot opt source destination
Chain ufw-after-logging-output (1 references)
target prot opt source destination
Chain ufw-after-output (1 references)
target prot opt source destination
Chain ufw-before-forward (1 references)
target prot opt source destination
ufw-user-forward all -- anywhere anywhere
Chain ufw-before-input (1 references)
target prot opt source destination
ufw-user-input all -- anywhere anywhere
Chain ufw-before-logging-forward (1 references)
target prot opt source destination
Chain ufw-before-logging-input (1 references)
target prot opt source destination
Chain ufw-before-logging-output (1 references)
target prot opt source destination
Chain ufw-before-output (1 references)
target prot opt source destination
ufw-user-output all -- anywhere anywhere
Chain ufw-logging-allow (0 references)
target prot opt source destination
Chain ufw-logging-deny (0 references)
target prot opt source destination
Chain ufw-reject-forward (1 references)
target prot opt source destination
Chain ufw-reject-input (1 references)
target prot opt source destination
Chain ufw-reject-output (1 references)
target prot opt source destination
Chain ufw-skip-to-policy-forward (0 references)
target prot opt source destination
DROP all -- anywhere anywhere
Chain ufw-skip-to-policy-input (7 references)
target prot opt source destination
DROP all -- anywhere anywhere
Chain ufw-skip-to-policy-output (0 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere
Chain ufw-track-forward (1 references)
target prot opt source destination
Chain ufw-track-input (1 references)
target prot opt source destination
Chain ufw-track-output (1 references)
target prot opt source destination
ACCEPT tcp -- anywhere anywhere ctstate NEW
ACCEPT udp -- anywhere anywhere ctstate NEW
Chain ufw-user-forward (1 references)
target prot opt source destination
Chain ufw-user-input (1 references)
target prot opt source destination
Chain ufw-user-limit (0 references)
target prot opt source destination
Chain ufw-user-limit-accept (0 references)
target prot opt source destination
Chain ufw-user-logging-forward (0 references)
target prot opt source destination
Chain ufw-user-logging-input (0 references)
target prot opt source destination
Chain ufw-user-logging-output (0 references)
target prot opt source destination
Chain ufw-user-output (1 references)
target prot opt source destination
gadget
July 3, 2023, 5:15pm
10
Did your previous YAML file include port binding declarations? e.g.:
ports:
- 8384:8384
Or did you set it as a start up option?
1 Like
MrChuw
July 3, 2023, 6:52pm
11
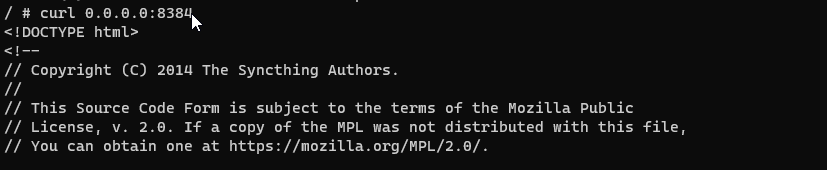
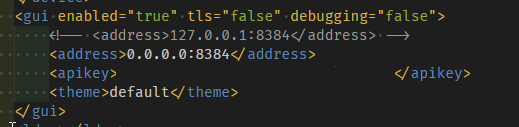
Oh my god, I understand what the problem is now. I had tried setting the port before and still couldn’t connect. Then I tried without specifying the port in the YAML file, and I didn’t realize that in the .xml configuration, for some reason, it was set to 127.0.0.1.
And when I changed it to 0.0.0.0, I didn’t realize that I also needed to specify the port again in the YAML file.
Thank you for your help. As usual, user error (? I assume he should have set it to 0.0.0.0, I don’t know why he didn’t).
1 Like
gadget
July 4, 2023, 1:50am
12
MrChuw:
Oh my god, I understand what the problem is now. I had tried setting the port before and still couldn’t connect. Then I tried without specifying the port in the YAML file, and I didn’t realize that in the .xml configuration, for some reason, it was set to 127.0.0.1.
It must have been manually changed to 127.0.0.1. Since the YAML file declares image: syncthing/syncthing:latest, it would have reverted back to the default of 0.0.0.0.
And when I changed it to 0.0.0.0, I didn’t realize that I also needed to specify the port again in the YAML file.
Thank you for your help. As usual, user error (? I assume he should have set it to 0.0.0.0, I don’t know why he didn’t).
With --network host and network_mode: host, the container’s network interface is mapped to the host’s. The net effect is that network services in the container are accessible without explicitly binding ports inside the container to the host.
If Syncthing’s config.xml has <address>127.0.0.1:8384</address>, on the host side Syncthing’s web GUI would be accessible at http://127.0.0.1:8384/. And if it’s <address>0.0.0.0:8384</address>, on the host side it would be accessible at http://0.0.0.0:8384/ (perhaps open to the rest of the LAN the host is connected to depending on the host’s firewall settings).
Or in other words, if the YAML file declares this…
network_mode: host
… port bindings aren’t needed:
ports:
- 8384:8384
But if host network mode isn’t used, then port bindings are required for access outside of the container.
system
August 3, 2023, 1:50am
13
This topic was automatically closed 30 days after the last reply. New replies are no longer allowed.