As recently disclosed by CERT-UA, Syncthing has been been used in combination with SPECTRE malware by the Vermin hacking group. What can be done to avoid and detect this malcious behavior?
According to this report [https://thehackernews.com/2024/06/spectr-malware-targets-ukraine-defense.html]
Attack chains commence with spear-phishing emails containing a RAR self-extracting archive file containing a decoy PDF file, a trojanized version of the SyncThing application that incorporates the SPECTR payload, and a batch script that activates the infection by launching the executable.
The attack uses a modified syncthing to do nefarious things. This technique can be applied to any computer program on any operating system that allows running untrusted code (i.e. Windows, Linux, macOS, iOS, Android…). It’s particularly easy for open source software though, since modifying them doesn’t require fiddling with machine code at all.
Syncthing signs all of its official binary releases using PGP. See syncthing security for details. So anyone modifying syncthing in any way will not have a correct signature - verifying syncthing releases obtained from somewhere can shed light on whether it has been modified or not.
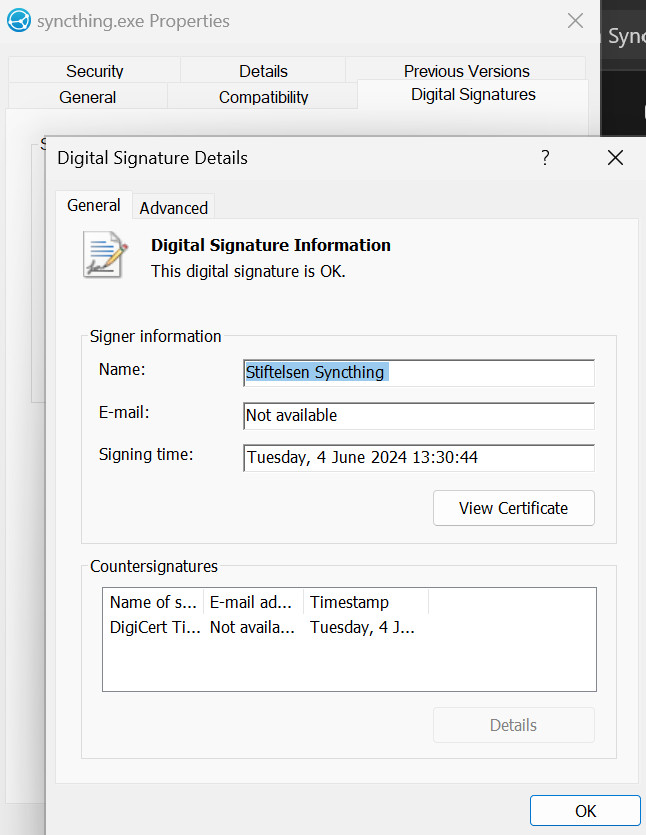
In addition, since this attack appears to target Windows computers, syncthing’s official Windows releases are also code signed with a Microsoft-trusted certificate (currently) issued to the Syncthing Foundation (Stiftelsen Syncthing). These signatures can also be verified, without requiring extra tools. Simply right-click the syncthing executable → Properties → Digital Signatures → Stiftelsen Syncthing → Details → “This digital signature is OK.”. Any tampered binary won’t have this.
thx a lot for the clarification!