Source: #7831
There are someone like me have own server running Syncthing for 24 hours. It brings convenience but also brings some potential security issues. The limitless attempt based on dictionary is.
It’s better to provide a secure feature that automatically bans these clients for a period of time while the consecutive failure of verification reaching a certain number of times.
Since the developers of Syncthing consider this as self-disposal, are there ways to get similar feature as simple as possible with outer solutions?
Temporarily my solution is to deny the access to port 8384 from ip on internet after GUI configured, and re-allow if need to configure again.
bt90
July 20, 2021, 5:16am
2
The simplest solution is to use a strong password. If i can guess your password in a reasonable amount of time, it’s way too easy.
1 Like
Why don’t you use a proper proxy with a fail2ban plugin or something?
Dose fail2ban has specialized plugin for Syncthing?
Why would it need to be syncthing specific? Nginx logs the responses from syncthing, can could ban clients that get repeated 401’s.
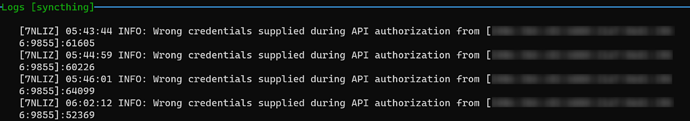
I’ve wrote Fail2ban configured files for it, but no date in timestamp format in Syncthing’s logs. So I have no idea how to get the next step.
Fail2ban Filter File
[Definition]
failregex = ^\[7NLIZ\].*Wrong credentials supplied during API authorization from \[?<HOST>\]?
ignoreregex =
Fail2ban Jail File
[syncthing-anti-401]
enabled = true
port = 8384
filter = syncthing-401
action = ufw[blocktype=reject,port=8384]
logpath = /path-to-logs/syncthing.log
bantime = 3600
findtime = 600
maxretry = 10
Syncthing Logs
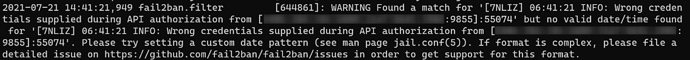
Fail2ban Error Messages
I customized date pattern, there are still errors due to date missing.
datepattern = %%H:%%M:%%S
I am not sure why you are trying to do it for syncthing, instead of doing it in nginx.
imsodin
July 21, 2021, 7:44am
10
To also get the date in logs you need to use the command-line flag --logflags=3.
I’ve tried in Nginx too, but seems still have to use with fail2ban.These are previous configs.
Filter File
[Definition]
failregex = ^<HOST>.*"(GET|POST).*" 401 .*$
ignoreregex =
Jail File
[nginx-anti-401]
enabled = true
port = 8384
filter = nginx-401
action = ufw[blocktype=reject,port=8384]
logpath = /var/log/nginx/access.log
bantime = 3600
findtime = 600
maxretry = 10
p.s. Nginx must be set to --net host if running as docker container.
Sure, yes, I am suggesting nginx + fail2ban as the way forward, as you can use nginx for rate limiting etc.
It does work! And I also found the other reason causing failure is different timezone settings between them.
So I reset timezone on Syncthing container and everything is running in expectations. All I could say is thanks!
1 Like
And thank you too, I marked it read later. Now I get two ways of solution. Will consider to use Nginx more as reverse proxy and explore its features.
1 Like