I have my own private discovery server, but if I enter this into my client it errors with:
global@https://<domain>: Post https://<domain>: remote error: tls: illegal parameter
Reverse proxy
stdiscosrv cmd: stdiscosrv -listen=:22068 -http
Apache reverse proxy (excerpt):
Include includes/ssl.conf # Configures ssl certificates, etc.
SSLProtocol TLSv1.3
ProxyPreserveHost On
ProxyRequests Off
RemoteIPHeader X-Forwarded-For
SSLVerifyClient optional_no_ca
RequestHeader set X-SSL-Cert "%{SSL_CLIENT_CERT}s"
RequestHeader set X-Forwarded-Proto "https"
ProxyPass / http://localhost:22068/
ProxyPassReverse / http://localhost:22068/
The apache docs describe SSL_CLIENT_CERT: https://httpd.apache.org/docs/2.4/mod/mod_ssl.html#envvars
And it logs this (in the access log):
<redacted> - - [09/Aug/2019:00:21:49 +0200] "GET /?device=<redacted> HTTP/1.1" 404 5424 "-" "Go-http-client/1.1"
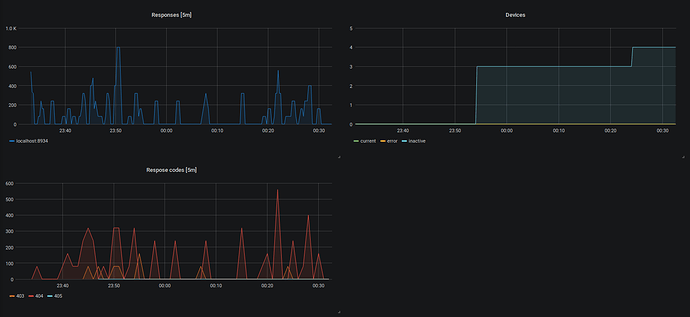
But no error. It seems to kind of work, because the stats show devices:
The discovery serve logs show no error:
Aug 08 23:13:53 <redacted> systemd[1]: Started Syncthing Discovery Server.
Aug 08 23:13:54 <redacted> stdiscosrv[1220]: stdiscosrv v1.0.1 (go1.11.5 linux-amd64) deb@build.syncthing.net 2019-01-18 10:34:18 UTC
Aug 08 23:13:54 <redacted> stdiscosrv[1220]: Server device ID is <redacted>
Inspecting the headers that the backend gets
Using a test server that just logs the headers
With curl and random client cert:
User-Agent: curl/7.58.0
Accept: */*
X-SSL-Cert: -----BEGIN CERTIFICATE----- <redacted> -----END CERTIFICATE-----
X-Forwarded-Proto: https
X-Forwarded-For: <redacted>
X-Forwarded-Host: <redacted>
X-Forwarded-Server: <redacted>
Connection: Keep-Alive
With syncthing:
User-Agent: Go-http-client/1.1
Accept-Encoding: gzip
X-SSL-Cert: (null)
X-Forwarded-Proto: https
X-Forwarded-For: <redacted>
X-Forwarded-Host: <redacted>
X-Forwarded-Server: <redacted>
Connection: Keep-Alive
So it looks like syncthing doesn’t send a client cert, but it is required to work correctly
Version Information
Syncthing Version: v1.2.1 (latest deb)
Stdiscosrv Version: v1.0.1 (latest deb)
OS Version: Ubuntu 18.04
Browser Version: N/A