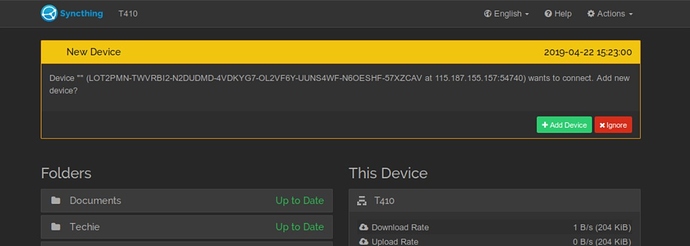
This appeared on my GUI today. How did this happen? Is someone trying to join my nodes? Curious.
Of course I rejected the invitation.Ok, no response.
So, I did not initiate this action. I have no new devices wanting to join with other nodes. Where did this request come from? (Was it because I posted this device identifier openly on this forum in response to another issue? If so, that was pretty stupid.)
UFW on the device in question is set to allows ST and SSH (port 22) only, connection to other devices at the time of this request was over my LAN but with connection to the internet. UPnP is enabled on my router.
ST has been working perfectly for me, but this is worrying.
Should I delete this device and reinstall ST (with new id string) and reconnect with other devices? Should I suck it up and move on?
Suck it up and move on. If it’s none of your devices it’s probably a portscan randomly hitting you and trying a HTTPS handshake. Syncthing is designed to resist that.
Ok, got it. Sucked up and moved on!
Thanks, Jakob.
I’ve recently tested this and discovered that syncthing is only showing this dialog if the other side sends a correct BEP-HELLO message. A simple TLS + random HTTP should have triggered the “unknown (newer?) protocol” message. At least that’s what I got when I tried this.
My guess is - yes. If you’re reachable via IP or relay (someone can get this info if he knows your device ID, or he can randomly try ip & port scans) someone can send your device a hello message which prompts this dialog.
If you don’t know the device address, simply ignoring it is fine (that causes syncthing to reject all connections from this device - but it will probably never try again anyway).
If you had accepted it, the dialog would have asked you what you want to share - so no folder would have been leaked before confirming twice, the other device could however learn what other devices you have in your cluster. Therefore ignoring is the best option - that way the other node can not even learn what the name of your device is.
Another thought I just had:
Syncthing immediatly sends a HELLO message after TLS is established, right? If you echo this exact message back - without actually knowing what it means - it should work, I guess. So a “smart portscan” could try this and unknowingly trigger this dialog.
Connection get’s rejected anyway, after exchaning the two HELLO messages.
Thanks, Max, for your explanation, that lessens my concerns. As I mentioned, I did post the device id on this forum in response to another question, so it may be random or it may be malicious.
To be honest, I’m surprised we don’t have more reports of people maliciously trying to access devices.
It’s a simple thing to do, and if someone accepts (and you request access to the default share and get that too), then you’ve potentially got access to some important documents.
I can easily imagine someone accepting if someone else set up Syncthing for them, and they’re just given this box that they don’t know anything about with a green button underneath it.
I’m not sure how to mitigate this without harming the usability story here. Perhaps something like only showing these dialogs when Syncthing is in some sort of “pairing” mode, or not showing them at all and instead showing a list of recent requests when someone tries to add a new device?
Could be. The name is empty, which might not mean anything but is at least the case when sending a hello to an unknown device.
I think that this attack, to the extent it is an attack, mostly depends on the default folder being in use. Removing that from our config makes it harder to trick the user even in the successful case. Given that you can’t reasonably guess an existing folder ID (apart from default) you’d have to just offer a random one and hope that the user accepts that and adds it as a new folder pointing to something interesting…
To be honest, I don’t think this is too far-fetched. Looking through my no-idea-what’s-going-on glasses, I can easily see a user saying to themselves “Documents – I’d better point this at my Documents folder, because it’s called ‘Documents’, and I need to put something”.
Yeah, entirely possible as well.
Just to clarify, the device id posted in another topic, is not the same as the device id of the machine ‘attacked’ in the first post here.
I don’t think that is true (might be wrong), as far as I recall other devices are only sent within the folder definition, so no folders = no devices.
Edit:
Confirmed if this is still up to date: Block Exchange Protocol v1 — Syncthing documentation
Yes. Unknown devices only get the Hello message, with the device name redacted. (They get the Syncthing version though.)
Known devices only get a Hello with the sender device name, and information about folders specifically shared with them. No folders shared, no further info given (an empty ClusterConfig).
Yeah it was a bit misleading what I wrote. I meant that if you add a device and share at least one folder (even if that’s empty), the other side could learn about other devices in the cluster (which also have this folder - for example the default folder). I just wanted to list a possible consequence other than leaking a folder’s data when sharing with an unknown party.
None of this applies if the user chooses to not click the add button and does not share any folders.
Just popping in to say I’ve had this happen twice this month, from the same unknown device.
A potential method of preventing people unknowingly adding a malicious device would be to display a message asking “Did you do this?” if a device tries to connect a certain amount of time, say a month, after syncthing folders / devices were last configured. Since the non techy people would usually set and forget their syncthing config a device randomly asking to connect a few weeks or a month later would usually be suspicious and a small warning message could prevent people from clicking Yes.
Another option is to hide these notifications entirely unless the user clicks a “show connection attempts” button of some sort.
That way if they’re setting up a new device/folder, then one device can prompt them to open up this list on the other device.
It’s slightly less user-friendly that the current situation, as it requires positive action by the user to see the list of devices which tried to connect. On the other hand, there’s close to zero chance of someone who doesn’t know what’s going on seeing a connection request from a malicious device.
This topic was automatically closed 30 days after the last reply. New replies are no longer allowed.