Anyways, I am suspect this is not the case as devices don’t advertise their names (atleast in that one screenshot)
Indeed, there is never a name associated with these (seemingly) random devices.
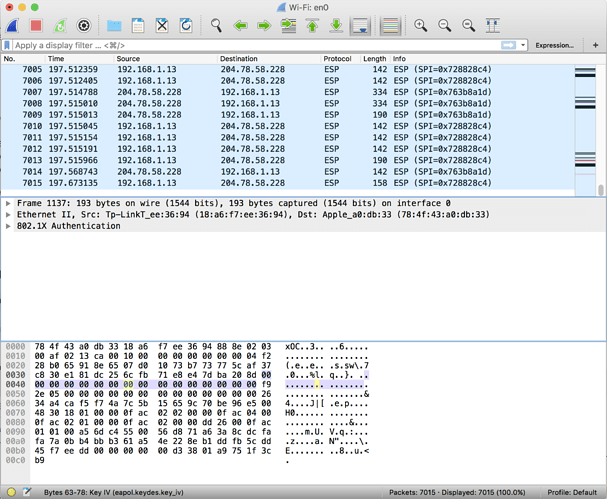
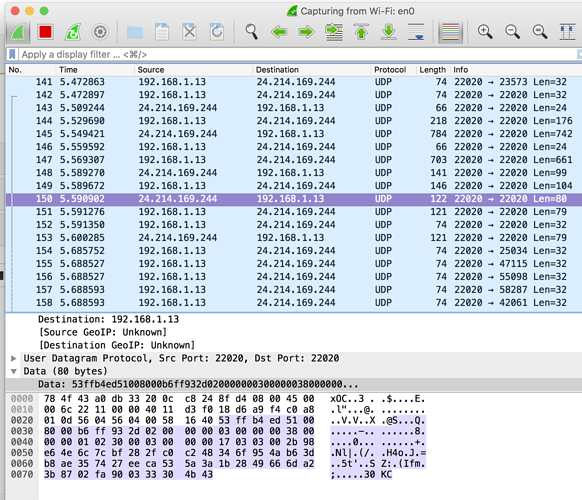
the logs around the time when these devices connected would help understand this better.
So, I ran syncthing -paths and got this:
Log file:
/Users/$USER/Library/Application Support/Syncthing/syncthing.log
When I try to access that location, it says it doesn’t exist however, and in-fact a search of my whole system returns nothing:
find ~/ -name "*syncthing.log" -type f 2> /dev/null
and
find / -name "*syncthing.log" -type f 2> /dev/null
exit with no output.
However, I was running syncthing from a terminal window I still had open, so I went in search of anything related to this mystery device. The only line referencing the Device ID is:
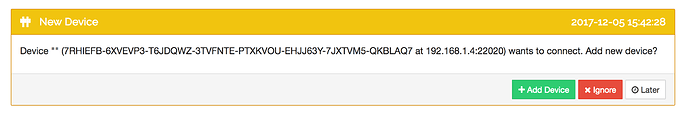
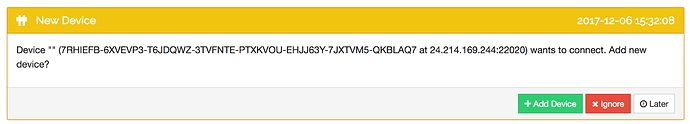
[N4JA2] 15:42:28 INFO: Connection from 7RHIEFB-6XVEVP3-T6JDQWZ-3TVFNTE-PTXKVOU-EHJJ63Y-7JXTVM5-QKBLAQ7 at 192.168.1.4:22020 (kcp-server) rejected: unknown device
Here are the surrounding lines from the log:
[N4JA2] 15:40:51 INFO: Failed to exchange Hello messages with LR76FOF-GR3QF4G-OUZUNYY-LWE3QSP-7HDM7IK-JWWSKF7-AOBHKSG-352LBAK (192.168.1.2:22000): read tcp 192.168.1.11:52124->192.168.1.2:22000: i/o timeout
[N4JA2] 15:41:50 INFO: Connection to AJ2GQWR-KDDYVYC-IQ74TAY-LTDYMGP-CVV43EJ-ZDIYPD2-T6ZSPYI-N76JYA2 closed: writing message: write tcp 192.168.1.11:22000->192.168.1.13:59484: write: can't assign requested address
[N4JA2] 15:41:58 INFO: Connection to XVD4YVE-ZZCYN54-FVJYIRP-V4L7T27-HXOONLY-IDQNE4A-LFSNEMM-QEPC7QD closed: writing message: write tcp 192.168.1.11:52002->192.168.1.8:22000: write: can't assign requested address
[N4JA2] 15:42:28 INFO: Connection from 7RHIEFB-6XVEVP3-T6JDQWZ-3TVFNTE-PTXKVOU-EHJJ63Y-7JXTVM5-QKBLAQ7 at 192.168.1.4:22020 (kcp-server) rejected: unknown device
[N4JA2] 15:48:48 INFO: Couldn't fetch release information: Get https://upgrades.syncthing.net/meta.json: dial tcp: lookup upgrades.syncthing.net: no such host
[N4JA2] 15:48:50 INFO: Exiting backoff state.
[N4JA2] 15:48:50 INFO: Relay listener (dynamic+https://relays.syncthing.net/endpoint) starting
[N4JA2] 15:48:51 INFO: Relay listener (dynamic+https://relays.syncthing.net/endpoint) shutting down
[N4JA2] 15:48:51 INFO: c.S.listenerSupervisor: Failed service 'dynamic+https://relays.syncthing.net/endpoint' (1.000000 failures of 2.000000), restarting: true, error: "{dynamic+https://relays.syncthing.net/endpoint dynamic+https://relays.syncthing.net/endpoint} returned unexpectedly", stacktrace: [unknown stack trace]
[N4JA2] 15:48:51 INFO: Relay listener (dynamic+https://relays.syncthing.net/endpoint) starting
[N4JA2] 15:48:51 INFO: Relay listener (dynamic+https://relays.syncthing.net/endpoint) shutting down
[N4JA2] 15:48:51 INFO: c.S.listenerSupervisor: Failed service 'dynamic+https://relays.syncthing.net/endpoint' (1.999965 failures of 2.000000), restarting: true, error: "{dynamic+https://relays.syncthing.net/endpoint dynamic+https://relays.syncthing.net/endpoint} returned unexpectedly", stacktrace: [unknown stack trace]
[N4JA2] 15:48:51 INFO: Relay listener (dynamic+https://relays.syncthing.net/endpoint) starting
[N4JA2] 15:48:51 INFO: Relay listener (dynamic+https://relays.syncthing.net/endpoint) shutting down
LR76FOF is a device running on the same network, but is using a VPN (so perhaps it’s connecting over the VPN?)
AJ2GQWR is a desktop wired into the same network the laptop you are reading the logs from is connected to (but over wifi.)
XVD4YVE is another desktop also wired into the same network. Note both desktops so far are connected through ethernet extenders that plug into wall sockets.
7RHIEFB is the mystery device asking to be added from the wi-fi extender’s IP address.